|
|
1. Basic Principles of Risk Management
a) Risk Management (RM) needs to be operationally integrated as a cross-cutting issue
- In routine project and portfolio management and steering,
- During the planning as well as the implementation phases,
- At different levels: project level, country level, headquarters and associated organisations.
b) Personal and institutional responsibilities and mandates need to be clarified and understood by stakeholders and decision makers on each level.
c) RM needs to become fully effective and proactive; moving from assessing and measuring risk to monitoring and progressing towards managing and reducing the risks.
d) Proactive management implies the necessity and readiness for flexible re-orientation and re-planning (strategic, personnel and operational) since conflict environments may change rapidly.
e) RM and conflict sensitivity (CS) can be mutually reinforcing (both negatively and positively) and needs to be cross-checked in a holistic manner. On the one hand, conflict sensitivity may increase the vulnerability towards threats (moving operations geographical into more conflict-affected areas might be considered as conflict-sensitive while increasing risks at the same time); and on the other, conflict sensitivity can also provide and promote a positive image of development work, thus reducing the vulnerability towards risks due to general acceptance among the stakeholders.
f) A variety of actors are involved in RM activities. Therefore, coordination and exchange of valuable information should be sought and the individual risk management system should be based on established instruments and mechanisms such as:
- Crisis planning and security provisions of diplomatic representations as well as
- Information systems and the monitoring of results by in-country representatives, implementing agencies and donors (UN-Office for the Coordination of Humanitarian Affairs (OCHA) and the European Commisison’s Humanitarian Aid Department (ECHO), and other coordination networks, etc.).
The design of a risk management strategy is usually highly situation-specific. Therefore, there is no single “right” approach. Rather individual, conceptual efforts are needed to develop consistent and effective risk management routines, and considering the existing linkages between the project and conflict in a given context. Hence, the consultation of professional expertise might be worthwhile, especially during the initial implementation phase.
Table 1: Basic components of risk management
1) Analysis & Monitoring
|
2) Prevention & Management |
- Security analysis
- Risk impact assessment
- Context monitoring, monitoring of security relevant changes and trends
- Regular meetings, flow of information
|
- Image and acceptance
- Protection
- Deterrence
- checklists
- security policies
- security manuals/Standard Operating Procedures (SOPs)
- security plan
- training (risk management, personal safety, negotiation skills, etc.)
- collaboration with other donors, diplomatic representations, etc.
- Advisory services
- working principles, code of conduct
- etc.
|
Adapted from Leonhardt et al. 2007: 114
3. Analysis and Monitoring
3.1 Security analysis
Risk management should be a proactive strategy, which minimises risks to staff, partners or beneficiaries who may become victims of psychological or physical violence as well minimising the risk to project assets. In crisis environments there is a heightened risk that projects may be directly targeted due to political or economic reasons and the possible projects’ linkage with the conflict. Additionally the risks from non-direct threats such as bomb blasts, mines, and cross-fires are comparatively high in certain contexts. Furthermore, exposure to high levels of crime in daily life, not only in (post-) conflict countries, may become a definite threat to persons and assets.
A security analysis examines and realistically assesses the situation and anticipated threats, vulnerabilities and the capacities of projects and staff to manage and minimise these risks appropriately. Depending on the level of threat, an analysis should be conducted by a security specialist. During the planning phase of programme and projects, a security analysis aims to assess whether appropriate framework conditions exist so that the feasibility of the planned intervention can be guaranteed. During the implementation phases, detailed analyses should be regularly conducted at programme/project levels and in the context of the immediate environments of the programme and project.
Figure 1: Framework of security analysis
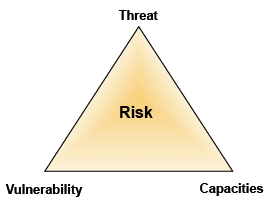
Risks are defined as the combination of threats, vulnerabilities and capacities where:
Threats: Are the potential dangers, harm and injuries to staff, partners, beneficiaries and project assets. Projects also face external dangers like land mines, being caught in cross-fires, attacks as well as from internal dangers, such as insensitive staff behaviour being “punished” by conflicting actors.
Vulnerabilities are: If staff, beneficiaries, partners and assets are exposed to threats because they are located, in conflict-affected areas, they become vulnerable. Vulnerability varies by organisational (image, strategy, activities, etc.) and individual factors (sex, age, level of training, job title, etc.).
Risk: Is being exposed to, or vulnerable to a threat that the staff, partners, beneficiaries, assets are at risk. If one is not exposed to a threat, then the risk factor is comparatively lower.
Capacities: Capacities are the resources and potentials that an organisation or an individual possesses in order to minimise and manage the vulnerability and exposure to threats through the strategies of acceptance, protection, and deterrence.
Capacity development in this regard can be achieved, for example, through the following:
- Staff training on risk management, communication, conflict transformation and personal safety,
- Regular assessment and gaining a thorough knowledge of the situation and the political, economic, and social contexts,
- Access to communication channels facilities and information, and
- Information-sharing with national and international stakeholders.
A risk management strategy aims to reduce the threat and vulnerability of an organisation and its staff, and to actively increase the organisations’ capacities to appropriately manage risk. That can contribute to reducing the exposure to threats and making risk levels acceptable.
3.2 Risk impact assessment
The likelihood of a danger and its possible impacts are crucial for the assessment of the situation. It may also influence the decisions on the level of risks acceptable to the project and staff. Therefore, risk impact assessments help projects and staff to clarify these issues by asking the following questions:
- How likely will a certain risk affect someone or something?
- If the likelihood is high, how serious will the impact be?
It is important to note that even for the same risks, different staff and project activities are likely to have different levels of acceptable risks and impacts. This can be due to external factors (such as. gender, ethnicity, age and the locations of project areas respectively, etc.) and internal factors (e.g. psychological experiences and modes of delivery respectively). Therefore, management and staff need to know the levels of acceptance and impact for each risk personally as well as project-wide. These also need to be monitored to alert managements when a risk shifts from being acceptable to unacceptable.
Generally, risks can be considered acceptable when
- There is little no concrete evidence that a project, its staff, beneficiaries or partners have been singled out for violence or serious intimidation;
- The staff can continue to work without being physically and psychologically harmed and the project assets are unharmed.
Generally, risks can be considered unacceptable when
- Staff, beneficiaries, partners and assets are harmed and become targets of specific threats, intimidations or violence;
- The assessment of the situation reveals that persons and assets will probably be harmed if the work continues without appropriate proactive measures.
Figure 2: The threshold of acceptable risks

The curved lines represent the thresholds for different risks. The threshold of acceptance varies with the risks’ probability and impacts. If a threat lies below the threshold of acceptable risk, actions are required to minimise the exposure to threats and to build capacities to manage them (see section 2 on risk prevention and management).
|
|

|
3.3 Context Monitoring
The anticipated threats, vulnerabilities and risks identified and assessed by the conflict and the security analyses need to be regularly monitored and evaluated in order to develop conscious and systematic management responses to the risks. These should comprise risk prevention and management strategies, policies, and procedures (see section 4). Regular context monitoring, therefore, is essential for preparing the ground for a well informed security analysis and risk impact assessment (section 3.1 and 3.2).
The following are some basic principles for context monitoring:
- Context monitoring traces security-relevant changes, trends, and anticipates the risks in general and in relation to the project’s/programme’s activities at different levels, i.e. political, economic and social. The areas of monitoring are defined by the conflict and security analyses.
- Context monitoring should be conducted on a country as well as at project/programme levels. Coordination and cooperation between different stakeholders at country level and joint analyses and discussions about perspectives on development work in crisis environments can contribute to ensuring cost-efficiencies and enhance the overall quality of monitoring.
- Monitoring should be undertaken during the planning and implementation phases of projects/programmes.
- Context monitoring on project/programme levels can be conducted either separately or as an integral part of the project/programme impact monitoring (e.g. by using check lists). The latter ensures that the context monitoring becomes a routine in project steering (see also ‘Participatory and Conflict Sensitive Impact Monitoring in Nepal’).
- Clear responsibilities for context monitoring and its evaluation have to be identified.
- Context monitoring can be performed at various levels of systematisation. Figure 4 shows a simple context monitoring format. In cases of relevant changes of the context more precise and in-depth investigations should be conducted to develop appropriate measures to reduce risks and manage them.
Table 2: Simple format for context monitoring
| Objectives, strategies and measures of DC (country level and/or project/programme level) |
Changes in contextual factors that are relevant to these objectives, strategies and measures
|
Risks and opportunities created by these changes in the environment
|
Options for risk reduction
|
| |
|
|
|
Leonhardt et al. 2007: 119
3.4 Regular meetings and flow of information
In order to properly evaluate and develop appropriate scenarios and actions/adjustments to the project and portfolio activities, regular review meetings should take place. These are best integrated into existing management and steering processes. The regular reporting, documentation, and analysis of the security situation should also be part of it. Moreover, the timely flow of information between the management team and the project’s field staff as well as to different security-relevant stakeholders and networks should also be ensured. Therefore, responsible management personnel must be present, accessible and well informed at all time. In many cases, project’s guards and drivers have proven to be valuable sources of up-to-date information “from the ground” due to their frequent contact with people resident in project implementation areas.
Box 1: Risk Management Office (RMO) in Nepal
|
 |
In Nepal, a comprehensive risk management and information system at country level was developed. The RMO was funded by DFID and GTZ, and was established in 2002 to deliver professional advisory services on risk and security management to programmes in order to enable and continue effective development amidst the escalating conflict without exacerbating it. It was decided to keep the RMO small in terms of human resources: the office employed one highly qualified external crisis manager, three national experts and some support staff. A network of emergency district coordinators from DFID, GTZ and other development agencies and organisations supported the office in providing its services, and this was an integral part of the information and contingency design of the RMO. The office’s core activities encompassed the mainstreaming of risk management into safe and effective development practices, providing situational analysis, security-related advisory services and information, as well as training to staff members, and acute crisis management. The major outputs were:
- Regular risk assessment reports and meetings: monthly national risk assessment, daily/weekly district situation reports, travel advice, and monthly RMO meetings,
- Trainings: basic and advanced risk management training, Safe and effective development in conflict (SEDC) training (see below),
- Crisis management guidelines and advice on how to deal with certain crisis situations,
- Best practices solutions and resources for Standard Operating Procedures (SOPs), contingency planning, etc.
|
 |
4. Prevention and Management
Generally, there are three strategies to reducing risks: (a) acceptance, (b) protection and (c) deterrence. A combination of acceptance and protection are the most common strategy applied. A public and transparent image of an organisation operating in conflict situation often builds the basis for reducing risks.
Figure 3: Means of risk reduction
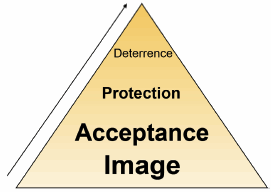
Adapted from DFID-LFP 2006: 39
4.1 Image and acceptance – the relevance of conflict sensitivity
The image of the operating agency/organisation is the foundation, on which a project gains acceptance. A good image can create acceptance, thus reducing risks. Without acceptance, other means of risk reduction are less effective. Furthermore, the project’s objectives and achievements may be jeopardised as well. For good and effective development practices In conflict situation, acceptance is a prerequisite. The linkages between risk management and conflict sensitivity become most evident when the project and its staff raise questions about how their image can be improved and what factors contribute to a good image. This leads back to maxim ‘do no harm’ which can be supported by checks and questions on resource transfers, implicit messages and connecting and dividing mechanisms:
- What and where do we deliver resources and support?
- Who benefits from resource transfers?
- Who implements what, and how is it implemented?
- Who is included, or excluded?
Box 2: Safe and effective development in conflict (SEDC)
|
| |
To support capacity building in conflict-sensitive development practices, the DFID/GTZ Risk Management Office (RMO) in Nepal developed a training approach on ‘safe and effective development in conflict (SEDC)’, which combined concepts of good development practice, risk management, to support the ‘do no harm’ philosophy. The training approach enabled programmes to make more realistic appraisals for their own organisations in the different working environments. Hence, organisation staff were made aware how their attitudes and behaviours affect their projects images and there acceptance. For the implementation agencies/organisations, it was essential to assess and understand themselves and the organisations they worked for, and to analyse their styles of working, how others might perceive them, and whether this placed them at risk.
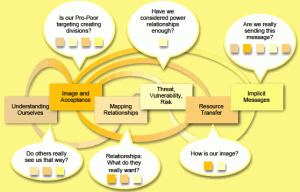
Since 2005, the RMO has provided training on SEDC to the staff of a variety of organisations, which helped them to identify and assess:
- A proper understanding of themselves (individual behaviour, language, origin, biography, etc.; organisational values, mandates, position in the conflict, funding sources, purpose and objectives);
- The personal and organisations’ image and its acceptance (what is the project doing: where, when, with whom, by whom, how, and why?);
- The nature of relationships with others (actors, relationships, interests, positions, needs);
- An understanding of the threats, vulnerabilities and risks;
- Resource transfers (type of resources, benefiting and non-benefiting groups, the project’s impartiality, connecting and dividing mechanisms and the positive and negative impacts of the transfers);
- The implicit messages of the projects and their staff (project design, strategiess, personal behaviours and working styles, involvement of local people, project’s responses to potential conflicts or expressed doubts, fears, and other obstacles).
Figure 4: The flexible process of SEDC
|
| |
4.2 Protection measures
Protection strategies generally consist of different components that are used in combination. Some examples of these are listed below.
Security procedures and documents: can provide guidance for both international and national staff. The development of such documents is a managerial responsibility. Inter-organisational coordination and exchanges of perceptions should be sought, especially regarding context monitoring (see above), so that duplication of work is avoided, analyses conducted are more thorough and reactions can be jointly organised at a quicker pace. A hierarchy of necessary documents can be developed, including:
- Security policy: providing overall policy guidance for the involved organisations , this should express the values and principles (such as the value of the lives of the staff is always precedence over the protection of material assets), the mission, vision and mandates of the involved organisation
- Standard Operating Procedures (SOPs, or security manual): providing generic procedures on how to handle risk situations. It needs to be adhered to by all staff in certain described and anticipated events, for example: preparation of field visits, travelling (by foot, or in vehicles), site security, communications, checkpoints, action in cases of sexual assault, abduction, extortion, etc. Questions asked should be : What should be done? How should it be done? Who is responsible for what if it happens?
- Security plans: entailing location-specific security information and procedures that are not part of the SOPs. It should be tailored to the particular context, taking into account the local situation, the characteristics of the staff, and regularly updated to take account of the changes of the findings of the security assessments and monitoring.
The security policy and plan should be short to increase the likelihood of all staff reading and referring to it. The SOPs might be longer as they describe many different security procedures that can be applied in various situations. Security plans and SOPs should be perceived as living documents that need to be adapted according to changes in the security situation and the demands of the project and its staff. Therefore, the design of the documents should be highly situation-specific as no single format will fits all situations.
The establishment and use of an information system is of overall importance and should cover the following at least
- Information on all staff (e.g. passport no., visa information, blood type, family contacts) and
- Contacts to support and safety networks that can assist in crisis situation (e.g. psychosocial counselling, etc.).
FAQ and training on basic negotiation skills: Negotiation is an aspect of effective communication. It is a discussion (formal or informal) to reach an agreement that is acceptable to both sides. Being able to negotiate with armed groups, for instance, is an essential skill to reduce vulnerability and risks to the project and oneself. During negotiations it is important to have clarity about the project, its objectives, mandate, modes of delivery etc. To guide staff during negotiations and to ensure consistency in the given answers and arguments, the development and dissemination of frequently asked questions to the staff is of importance Awareness raising through trainings on principles, image and acceptance of the project’s work is also essential. However, to become effective as a means of risk reduction, the answers need to be understood, internalised and consistently used by all staff and be updated frequently.
Working principles and codes of conduct: The basic principles of independence, impartiality, neutrality, and transparency should create the basis for project-specific working principles adapted to local contexts (e.g. guidelines for cooperation). Being impartial, independent and striving for neutrality helps to reduce risks. Transparency, therefore, may demonstrate the project’s impartiality, and enhance its acceptance. This may increase the positive image of staff and the project. Furthermore, participation, accountability as well as quick and visible impacts should be part of the principles:
- Independence: Formulate and implement objectives, policies and strategies independently and without interference of the conflicting parties.
- Impartiality: The provision of assistance on the basis of needs without any form of discrimination regarding gender, age, origin, beliefs, political opinion etc. In the case of development cooperation, assistance to the neediest persons may be based on the concept of affirmative action (e.g. women as a special target group). However, in order to avoid any contradiction to the principle of impartiality the selection of the target groups needs to be conducted solely on the basis of needs in the first place. This leads to the principle of neutrality.
- Neutrality: Development work, in contrast to humanitarian aid, is a political endeavour, which strives to work on political, social and economic reforms by promoting fundamental rights such as human rights and the rule of law. Therefore development work in the first place can’t claim to be neutral, but it needs to ensure that this does not jeopardise the ability to provide fair assistance to those most in need. Furthermore, in conflict environments development work should not take sides.
- Transparency: A transparent project planning, implementation and steering process ensures and demonstrates that services are provided fairly.
- Participation and accountability: Participation should be ensured during the planning and implementation phases, thus promoting accountability and ownership by the beneficiaries. Targeting mechanisms and modes of delivery should be developed in a participatory manner and transparently communicated to all relevant stakeholders.
- Quick and visible impact helps to further increase the image and acceptance of the project and its staff.
Cooperation with other agencies, including joint analyses and discussions about perceived risks as well as agreement on Basic Operating Guidelines (BOG) or general codes of conducts (e.g. IFRC, SPHERE) by several organisations and agencies should be sought. Less plurality and more clarity will strengthen the impact and effectiveness of working principles. BOGs and general codes of conduct provide a broader framework, to which project specific principles can be linked. However, principles can only reduce vulnerability and risk when they are strictly followed. Therefore, it is crucial to train the staff on them and to ensure that the principles are properly understood by all. The guidelines also need to be disseminated and communicated openly to all stakeholders (beneficiaries, other agencies, conflicting parties, etc.).
Box 3: Basic Operating Guidelines (BOG) in Nepal
|
| |
In Nepal, Basic Operating Guidelines (BOG) were developed by 10 international agencies in 2003 to; ensure the safety of staff; an environment to effectively carry out activities In amidst the conflict ,and to set minimum standards for their programs and staff at the field level. After consultation with the conflicting parties both the Government of Nepal and the People’s Liberation Army eventually agreed to respect the BOGs. Generally, any replication of this instrument depends on the degree of donor coordination and the willingness of the conflicting parties to agree and to cooperate in this regard. The BOGs stated that:
- We are in Nepal to contribute to improvement in the quality of life of the people of Nepal. Our assistance focuses on reducing poverty, meeting basic needs and enabling communities to become self-sufficient.
- We work through the freely expressed wishes of local communities, and we respect the dignity of people, their culture, religion and customs.
- We provide assistance to the poor and marginalized people of Nepal, regardless of where they live and who they are. Priorities for assistance are based on need alone, and not on any political, ethnic or religious agenda.
- We ensure that our assistance is transparent and we involve poor people and their communities in the planning, management and implementation of programmes. We are accountable to those whom we seek to assist and to those providing the resources.
- We seek to ensure that our assistance tackles discrimination and social exclusion, most notably based on gender, ethnicity, caste and religion.
- We recruit staff on the basis of suitability and qualification for the job, and not on the basis of political or any other considerations.
- We do not accept our staff and development partners being subjected to violence, abduction, harassment or intimidation, or being threatened in any manner.
- We do not work where staff are forced to compromise core values or principles.
- We do not accept our assistance being used for any military, political or sectarian purposes.
- We do not make contributions to political parties and do not make any forced contributions in cash or kind.
- Our equipment, supplies and facilities are not used for purposes other than those stated in our programme objectives. Our vehicles are not used to transport persons or goods that have no direct connection with the development programme. Our vehicles do not carry armed or uniformed personnel.
- We do not tolerate the theft, diversion or misuse of development or humanitarian supplies. Unhindered access of such supplies is essential.
- We urge all those concerned to allow full access by development and humanitarian personnel to all people in need of assistance, and to make available, as far as possible, all necessary facilities for their operations, and to promote the safety, security and freedom of movement of such personnel.
- We expect and encourage all actors concerned to comply strictly with international humanitarian principles and human rights law.
Agreed to by: UN, EC, Danida, SDC, CIDA, Norwegian Embassy, DFID, AusAID, JICA, GTZ, Embassy of Finland, SNV, Association of international NGOs in Nepal
|
| |
Other protection measures:
- Further training on personal safety and crisis management;
- Reduction of the staff’s exposure to risk through imposing no-go areas and no-go times;
- Reduction or increase of visibility and profile: in some situations, the staff might increase protection by displaying the emblem of the organisation; in other cases, it might be better to keep a low profile with regards to residence, means of transport, personnel appearance and behaviour;
- Depending on the context, the development of a public communication strategy might be worthwhile
- Use of protective devices such as helmets, bomb shelters, wires, etc.
4.3 Deterrence (as last resort)
Deterrence measures are usually used as a last resort where acceptance and protection measures fail to reduce risks to staff and assets. In general, two measures can be distinguished:
- Legal, political and economic sanctions to repress the perpetrators of violence.
- Suspension of operations and/or withdrawal: Experiences have shown that suspension as a deterrence tactic seems to work best when there is a high level of acceptance of the project’s work. Besides the most important question on staff safety, suspension and withdrawal might also be a last resort when the conflict parties interfere with development work so that working principles and the achievement of the objectives can’t be guaranteed anymore. However, the suspension of activities will likely have impacts on the development space, i.e. room for manoeuvre, as a whole and the way the conflict parties will deal with other organisations in the future. This also needs to be kept in mind and, at best, discussed and coordinated with other stakeholders and partners.
|






